Are you interested in investing in cryptocurrency but worried about falling victim to a scam? The world of digital assets is exciting, but it also attracts fraudulent schemes. This article will cover five common cryptocurrency scams, providing you with the knowledge and awareness needed to protect yourself from cryptocurrency fraud and make safe investments. Learn how to identify red flags and avoid losing your hard-earned money to crypto scams.
Phishing Scams and Fake Websites
Phishing is a type of online fraud where malicious actors attempt to trick individuals into revealing sensitive information such as usernames, passwords, credit card details, or social security numbers. This is often achieved through deceptive emails, text messages, or websites that mimic legitimate organizations.
Fake websites are a common tactic employed in phishing scams. These websites are designed to look almost identical to legitimate websites, often including similar logos, color schemes, and even web addresses that are subtly altered. Users who unintentionally visit these fraudulent sites may be prompted to enter their login credentials or other personal information, which is then captured by the attackers.
The consequences of falling victim to a phishing scam can be severe. Victims may experience identity theft, financial loss, and reputational damage. Furthermore, the compromised information could be used for further malicious activities, such as spreading malware or launching additional attacks.
Protection against phishing scams and fake websites requires vigilance and awareness. Users should be cautious of unsolicited emails or text messages requesting personal information. They should carefully examine website URLs for any inconsistencies or suspicious elements. Hovering over links before clicking can reveal the actual destination URL. Employing strong passwords, regularly updating software, and using reputable anti-virus software are also crucial preventative measures.
Educational initiatives play a significant role in mitigating the risks associated with phishing scams. Raising public awareness about the tactics employed by phishers and providing users with the knowledge and skills to identify and avoid these scams are essential steps in combating this pervasive form of cybercrime. Organizations should invest in cybersecurity training for their employees to reinforce best practices and enhance their ability to recognize and report phishing attempts.
In conclusion, understanding the methods used in phishing scams and learning how to identify fake websites are crucial for protecting oneself online. By staying informed and practicing safe online habits, individuals can significantly reduce their risk of becoming victims of this increasingly sophisticated form of cybercrime.
Ponzi and Pyramid Schemes

Ponzi schemes and pyramid schemes are both fraudulent investment operations that promise high returns with little to no risk. They both rely on recruiting new investors to pay off earlier investors, creating an unsustainable system destined to collapse. However, there are key distinctions between the two.
A Ponzi scheme generates returns for older investors by acquiring new investors. The operator, often a charismatic individual, uses funds from newer investors to pay profits to older investors. The scheme’s profitability is entirely dependent on a constant influx of new capital; there is no legitimate underlying business or investment strategy generating profits. Instead, it’s a deceptive cycle of paying existing investors with money from new investors. When the flow of new money dries up, the scheme inevitably implodes.
A pyramid scheme, while also fraudulent, focuses on recruitment rather than investment. Participants pay an upfront fee to join, and their profit is derived solely from recruiting new members. There is no actual product or service being sold; the focus is entirely on expanding the pyramid. Unlike a Ponzi scheme, which may involve a seemingly legitimate investment, a pyramid scheme’s fraudulent nature is often more readily apparent due to its emphasis on recruitment over any tangible product or service. The vast majority of participants in a pyramid scheme inevitably lose money.
Key Differences Summarized: While both are illegal and unsustainable, a Ponzi scheme focuses on generating returns through fictitious investments, while a pyramid scheme relies on recruiting new members for profit. A Ponzi scheme may involve a more complex facade of investment activity, whereas a pyramid scheme’s reliance on recruitment is often more transparent. Both, however, share the common trait of ultimately collapsing when the influx of new money ceases.
Identifying Red Flags: High, unrealistic returns, lack of transparency regarding investment strategies, pressure to invest quickly, promises of easy money, and emphasis on recruiting new members are all red flags indicating a potential Ponzi or pyramid scheme. Always conduct thorough due diligence before investing and be wary of any opportunity that promises exceptionally high returns with minimal risk. If something sounds too good to be true, it probably is.
Rug Pulls in DeFi and Decentralized Finance (DeFi) and Non-Fungible Tokens (NFTs)

The decentralized finance (DeFi) and non-fungible token (NFT) spaces, while offering exciting opportunities for innovation and investment, are also susceptible to malicious activities. One particularly damaging practice is the rug pull, a type of exit scam that leaves investors with significant losses.
A rug pull occurs when the developers of a DeFi project or NFT collection suddenly and unexpectedly withdraw all the funds invested by users, leaving the project worthless. This often involves draining liquidity pools, halting trading, and abandoning the platform, leaving investors with nothing but worthless tokens.
Rug pulls are facilitated by the pseudonymous and decentralized nature of many DeFi and NFT projects. The lack of stringent regulations and the ease of creating and deploying tokens on blockchain networks create opportunities for fraudulent actors to operate with relative impunity.
Several red flags can indicate a potential rug pull. These include an anonymous development team, a lack of transparency about the project’s code and financials, unrealistic promises of high returns, and a sudden surge in trading volume followed by a sharp decline.
Protecting yourself from rug pulls requires thorough due diligence. This includes researching the project’s team, examining the smart contract code for vulnerabilities, and understanding the project’s tokenomics. Diversifying investments and only investing what you can afford to lose are crucial risk mitigation strategies.
The consequences of rug pulls can be devastating, leading to substantial financial losses for investors and eroding trust in the DeFi and NFT ecosystems. Increased awareness, stricter community scrutiny, and improved regulatory frameworks are necessary to mitigate the risk of these malicious activities.
While the DeFi and NFT spaces hold immense potential, it’s crucial to approach them with caution and awareness of the risks involved. Thorough due diligence, careful investment strategies, and community vigilance are essential in protecting investors from the damaging effects of rug pulls.
Fake Airdrops and Giveaway Scams
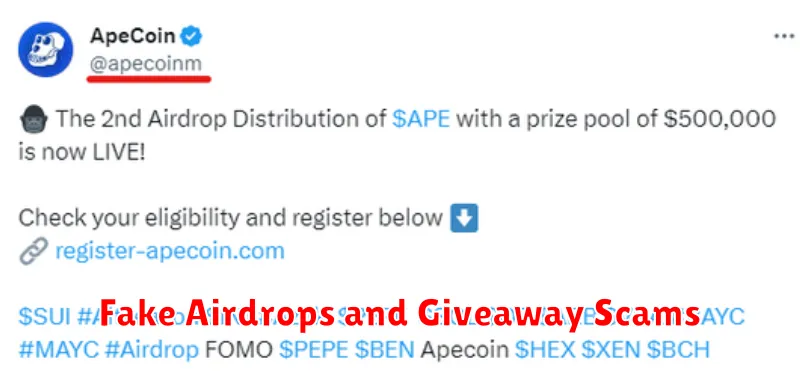
The cryptocurrency space, while offering immense potential for financial growth, is unfortunately rife with fraudulent activities. One prevalent scam targets unsuspecting investors through the promise of free cryptocurrency airdrops or giveaways.
These scams typically operate through various channels, including social media platforms, messaging apps, and even fake websites mimicking legitimate cryptocurrency projects. Fraudsters often leverage the excitement surrounding new cryptocurrencies or popular projects to lure victims with seemingly unbelievable opportunities.
The mechanics of these scams are often quite similar. Victims are enticed to participate by completing certain tasks, such as following social media accounts, retweeting messages, or sending small amounts of cryptocurrency to a designated address. In return, they are promised a significantly larger sum of cryptocurrency – a return that is far too good to be true.
However, once victims complete these tasks, they receive nothing. The fraudsters disappear with the collected cryptocurrency, leaving victims with nothing but a financial loss and a potentially compromised online presence due to the sensitive information they may have shared. Furthermore, these scams can also lead to identity theft and other serious consequences.
Identifying fake airdrops and giveaways requires a critical and cautious approach. Always verify the legitimacy of any airdrop or giveaway offer through the official channels of the cryptocurrency project in question. Legitimate projects will rarely promote their airdrops via unsolicited messages or through unofficial channels.
Be wary of unrealistic promises of high returns and requests for personal information or cryptocurrency payments. Never send cryptocurrency to addresses you are not entirely sure about. Exercise due diligence and protect yourself from these fraudulent schemes by verifying the sources of information and acting with caution.
In conclusion, while the allure of free cryptocurrency is tempting, vigilance is paramount. Remain skeptical, verify information, and prioritize your security to avoid falling victim to fake airdrops and giveaway scams.
Social Engineering and Fake Support Scams

Social engineering is a deceptive manipulation technique used to trick individuals into divulging confidential information or performing actions that compromise their security. These scams often leverage psychological manipulation to exploit human trust and vulnerabilities. Fake support scams are a particularly prevalent form of social engineering, often targeting unsuspecting computer users or mobile device owners.
Scammers employ various tactics to appear legitimate. They might initiate contact through unsolicited phone calls, emails, or pop-up messages, pretending to represent a reputable technical support organization like Microsoft, Apple, or a well-known antivirus company. Their goal is to gain access to your system or obtain sensitive information like credit card details, passwords, or bank account numbers.
These scams often involve creating a sense of urgency or panic. The scammer might claim that your computer is infected with a virus, that your operating system is outdated, or that your online accounts are compromised. They may even fabricate technical errors to further convince you of their supposed expertise. The ultimate goal is to manipulate you into installing malicious software, providing remote access to your computer, or paying for unnecessary services.
Identifying these scams requires vigilance and critical thinking. Legitimate support organizations will rarely contact you proactively. They will typically only provide support if you initiate contact through their official channels. Be wary of unsolicited calls or messages claiming urgent technical issues. Never provide personal information to unsolicited callers or those claiming to represent a company unless you’ve independently verified their identity through official channels.
Protecting yourself from these scams involves educating yourself on common tactics. Be suspicious of unsolicited contact, verify the identity of any caller claiming to be from a technical support company, and never provide remote access to your computer unless you are absolutely certain of the individual’s identity and legitimacy. Consider installing reputable antivirus software and keeping your operating system and applications up-to-date to minimize vulnerabilities.
In short, awareness and caution are your best defenses against social engineering and fake support scams. By understanding the tactics employed by scammers and adopting proactive security measures, you can significantly reduce your risk of becoming a victim.
