This article explores the 5 key features that define blockchain technology and drive its transformative potential across diverse industries. We delve into the core components that make blockchain a secure, transparent, and efficient system, examining its decentralized nature, immutability, cryptographic security, transparency, and smart contract functionality. Understanding these key features is crucial for anyone seeking to grasp the implications of this revolutionary technology and its impact on the future of data management, financial transactions, and beyond.
Decentralization for Transparency
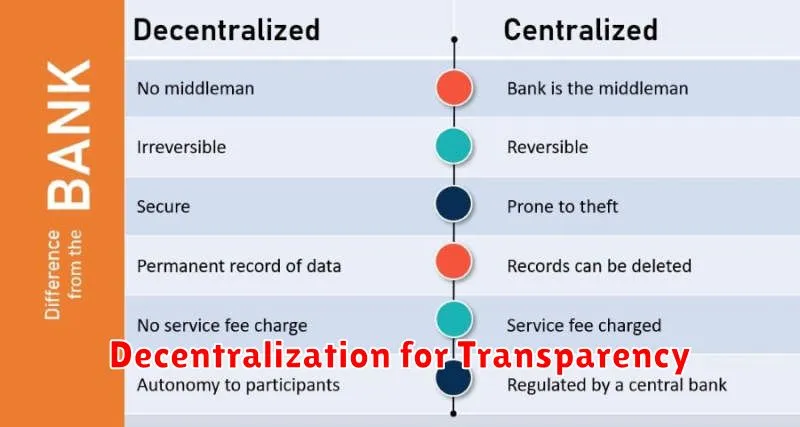
Decentralization offers a powerful approach to enhancing transparency within organizations and systems. By distributing control and decision-making power away from a central authority, it fosters a more open and accountable environment. This shift can lead to increased trust and greater participation from stakeholders.
One key benefit of decentralized systems is the increased visibility of processes and data. When information is not confined to a single point of control, it becomes more readily accessible to those who need it. This openness can prevent manipulation and improve the accuracy of information flow.
Furthermore, accountability is significantly strengthened through decentralization. Because actions and decisions are more readily traceable to specific individuals or groups, there is a greater incentive for responsible behavior. This reduces the risk of corruption and mismanagement.
However, the implementation of decentralized systems presents challenges. Coordination and communication can become more complex, requiring robust mechanisms to ensure efficient collaboration across different entities. The potential for inconsistencies and fragmentation also needs to be carefully addressed through clear guidelines and standardized procedures.
Despite these challenges, the advantages of transparency achieved through decentralization are substantial. In areas such as governance, finance, and supply chains, decentralized systems can promote greater trust, efficiency, and fairness. As technology continues to evolve, we can expect to see increasingly sophisticated decentralized solutions that further enhance transparency and accountability across various sectors.
Smart Contracts for Automation
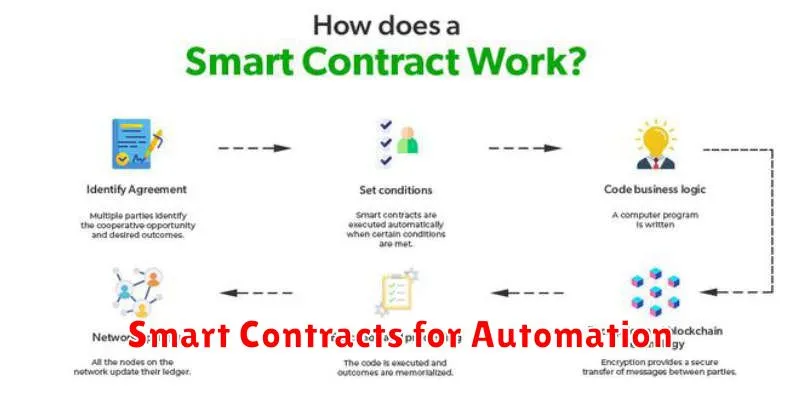
Smart contracts represent a groundbreaking technology with the potential to revolutionize various sectors by automating agreements and processes. They are self-executing contracts with the terms of the agreement between buyer and seller being directly written into lines of code.
The core functionality lies in their automation capabilities. Once predefined conditions are met, the contract automatically executes, eliminating the need for intermediaries and significantly reducing delays and disputes. This automation enhances efficiency and transparency, making transactions faster and more reliable.
Decentralization is another key aspect. Smart contracts typically reside on blockchain networks, ensuring immutability and preventing unauthorized alterations. This fosters trust and security, as all parties involved have access to a shared, verifiable record of the agreement.
However, the implementation of smart contracts requires careful consideration. Security vulnerabilities are a significant concern; poorly written code can be exploited, leading to financial losses or breaches of confidentiality. Furthermore, the legal enforceability of smart contracts is still evolving, and legal frameworks are adapting to this innovative technology.
Despite these challenges, the potential benefits of smart contracts are substantial. Their application spans diverse domains, including supply chain management, finance, healthcare, and voting systems. As the technology matures and regulatory clarity emerges, smart contracts are poised to play an increasingly crucial role in shaping the future of automated agreements.
Immutability for Data Security

Immutability, in the context of data security, refers to the inability of data to be modified after its creation. This characteristic provides a powerful defense against various threats, significantly bolstering overall data security posture.
One key advantage of immutability is its resistance to data breaches. Since immutable data cannot be altered, even if a malicious actor gains unauthorized access, they cannot modify sensitive information. This prevents data corruption, manipulation, and the potential for exfiltration of compromised data.
Furthermore, immutability offers robust protection against ransomware attacks. Because the original data remains unchanged, attackers are unable to encrypt or delete it, rendering their extortion attempts ineffective. Recovery from a ransomware attack becomes significantly simpler and faster, as the original, uncorrupted data is readily available.
The principle of immutability is often implemented using various techniques, including blockchain technology, data versioning, and write-once-read-many (WORM) storage. Each of these methods provides different levels of immutability, tailored to specific security needs and infrastructure constraints.
While immutability provides strong security benefits, it’s crucial to acknowledge some limitations. Managing large volumes of immutable data can pose storage challenges and may require specific infrastructure and management practices. Additionally, the inability to update data necessitates careful planning and robust data governance policies.
In conclusion, immutability is a valuable tool in the arsenal of data security strategies. Its inherent resistance to data breaches and ransomware attacks makes it a critical element for organizations seeking to strengthen their overall security posture. However, a thoughtful consideration of its limitations and the implementation of appropriate management practices is crucial for successful integration into any security framework.
Cryptographic Encryption for Privacy
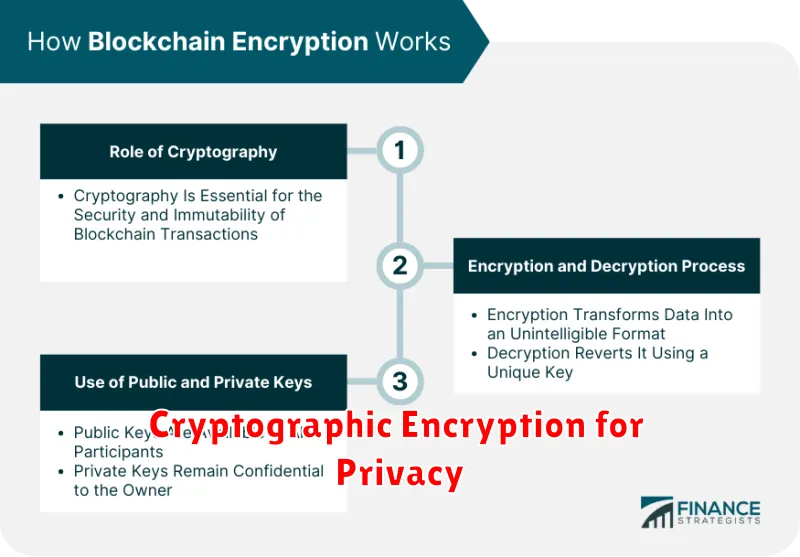
Cryptographic encryption is a cornerstone of modern data security, providing a crucial mechanism for protecting sensitive information from unauthorized access. It involves transforming readable data, known as plaintext, into an unreadable format, called ciphertext, using a specific algorithm and a secret key.
The strength of encryption hinges on the complexity of the algorithm and the security of the key. Robust algorithms, like those used in Advanced Encryption Standard (AES) and RSA, are computationally difficult to reverse without possessing the correct key. This ensures that even if intercepted, the ciphertext remains unintelligible to unauthorized parties.
There are two primary types of encryption: symmetric-key encryption and asymmetric-key encryption. Symmetric-key encryption utilizes the same key for both encryption and decryption, making it efficient but requiring secure key exchange. Asymmetric-key encryption, on the other hand, employs a pair of keys: a public key for encryption and a private key for decryption. This eliminates the need for secure key exchange, as the public key can be widely distributed.
Digital signatures, a crucial application of asymmetric encryption, provide authentication and integrity verification. They allow the recipient to confirm the sender’s identity and ensure the message hasn’t been tampered with during transmission. This is critical for secure online transactions and communication.
Despite its effectiveness, encryption is not foolproof. Weaknesses in algorithm design, implementation errors, or compromised keys can compromise security. Therefore, it’s crucial to utilize strong encryption algorithms, implement secure key management practices, and stay updated on the latest cryptographic best practices to maintain robust data privacy.
In conclusion, cryptographic encryption plays a vital role in protecting privacy in the digital age. Its continued development and proper implementation are essential for securing sensitive information and mitigating the risks of unauthorized access and data breaches.
Scalability Solutions for Mass Adoption

Mass adoption of any technology, particularly blockchain-based systems, hinges on achieving scalability. This means the system must be able to handle a significantly increasing number of users and transactions without compromising performance or security. Current limitations often manifest as slow transaction speeds and high fees, hindering widespread use.
Several approaches address scalability challenges. Layer-1 solutions directly modify the core protocol of the blockchain itself. This can involve enhancing consensus mechanisms to process transactions more efficiently or increasing block sizes to accommodate more data. However, Layer-1 changes often require significant upgrades and consensus among network participants.
Layer-2 solutions, conversely, build on top of the existing blockchain infrastructure. These solutions often involve techniques such as state channels, which allow multiple transactions to occur off-chain before being settled on the main chain, or rollup solutions that bundle numerous transactions into a single transaction for processing. Layer-2 scaling offers a more flexible and faster route to increased capacity, avoiding the complexities of direct protocol alterations.
Sharding is another prominent technique gaining traction. This involves dividing the blockchain into smaller, more manageable pieces (shards), allowing parallel processing of transactions. Each shard can operate independently, significantly boosting throughput. However, implementing sharding effectively requires careful design to maintain data consistency and security across shards.
The choice of scalability solution depends on various factors including the specific requirements of the blockchain, the level of decentralization desired, and the technical expertise available. A hybrid approach, combining different solutions, may often prove to be the most effective strategy in tackling the complex issue of scaling for mass adoption.
Ultimately, successful scalability solutions must strike a balance between speed, security, and decentralization. Ongoing research and development in this area are crucial for unlocking the full potential of blockchain technology and paving the way for its widespread acceptance.
